Description
This article describes the configuration of the FortiGate SNMP agent so that Domotz can retrieve device data via the SNMP protocol. It requires configuration on both the FortiGate and Domotz sides.
FortiGate configuration
The FortiGate SNMP configuration can be performed in two ways: either through the Graphical User Interface (GUI) or the Command Line Interface (CLI).
FortiGate SNMP configuration requires the following two mandatory steps:
⦁ Enable SNMP protocol on FortiGate port
⦁ Enable SNMP agent and configure the SNMP connection details
FortiGate configuration via GUI
– Enable SNMP protocol on FortiGate port:
Log in the FortiGate GUI using an administrator user and navigate to the “Network / Interface” section.
Identify the Firewall interface or port or VLAN that will be used by the Domotz collector to query the FortiGate via SNMP. Let’s assume for the scope of this article that it is “port 1”:
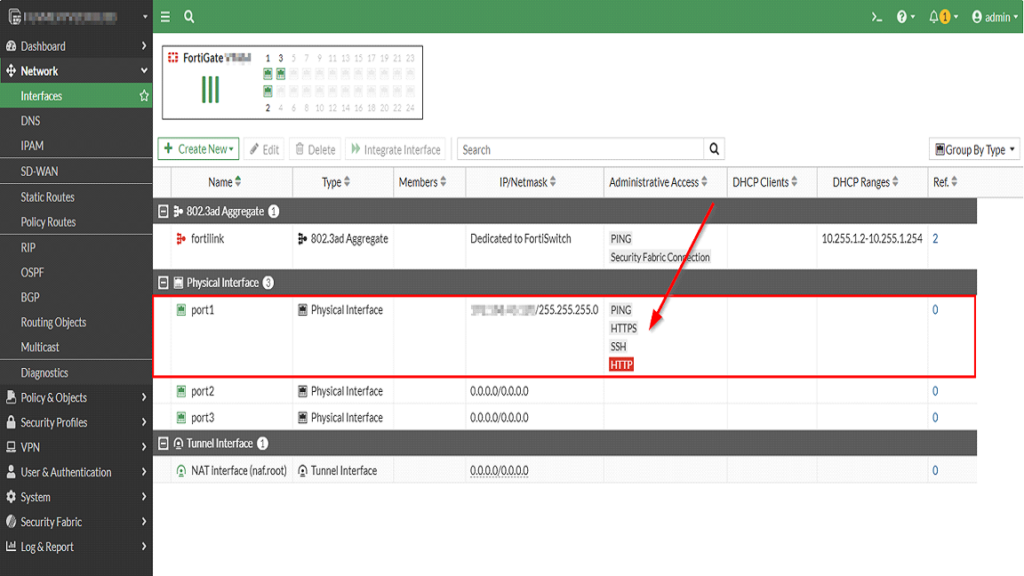
SNMP is not normally enabled by default, so it requires to be set explicitly.
Edit the “port 1” by double clicking the line or using right-click on it:
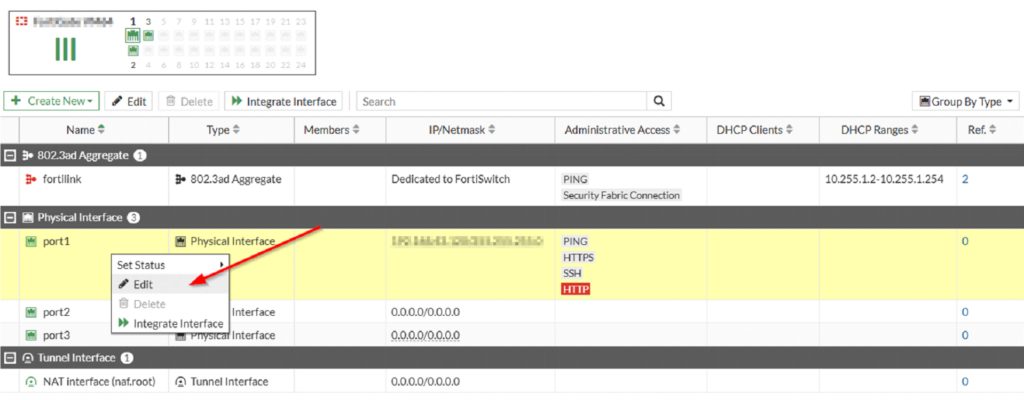
The following page appears. Enable SNMP protocol in the “Administrative Access” section as shown in the following image:
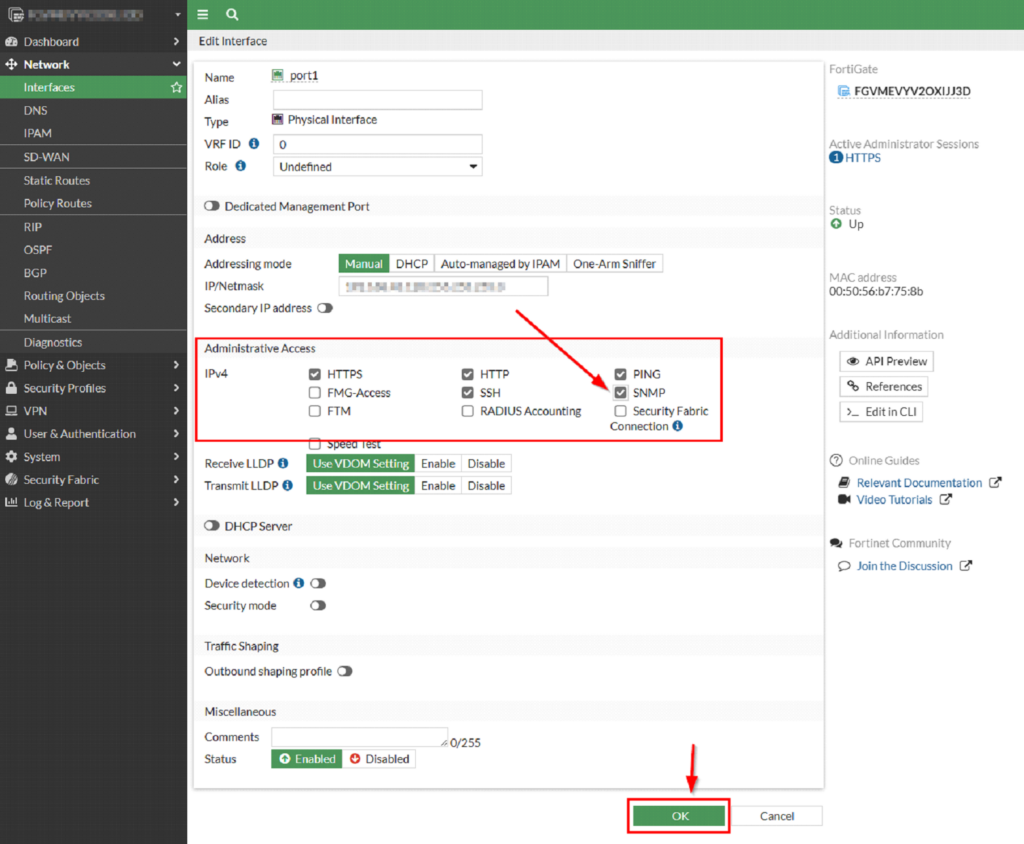
Then press OK button on the bottom of the page, read the configuration page that might appear and if ok then Confirm that you want to proceed.
After this process, SNMP administrative access will be enabled on the port and the interface page looks like the following:
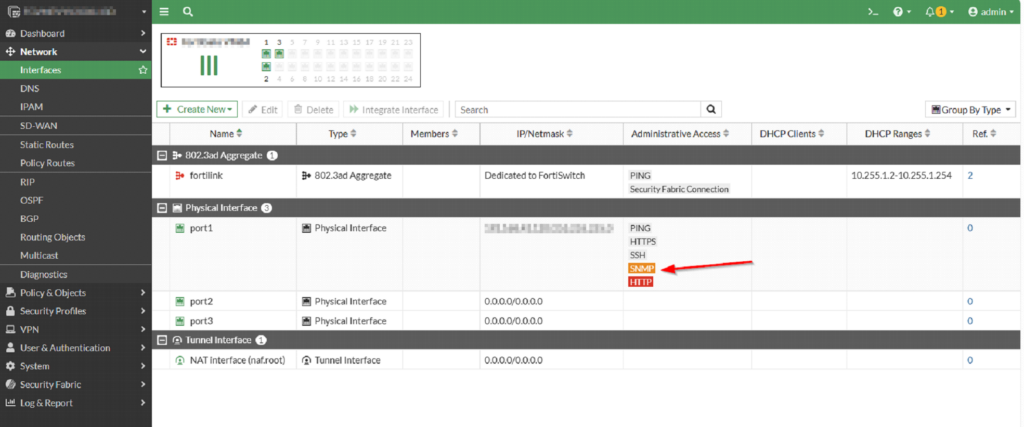
– Enable SNMP agent and configure the SNMP connection details:
This example uses SNMP v3 between Domotz and FortiGate. SNMP v3 is recommended SNMP version of important network devices.
The configurations are in the “System / SNMP” page as depicted below.
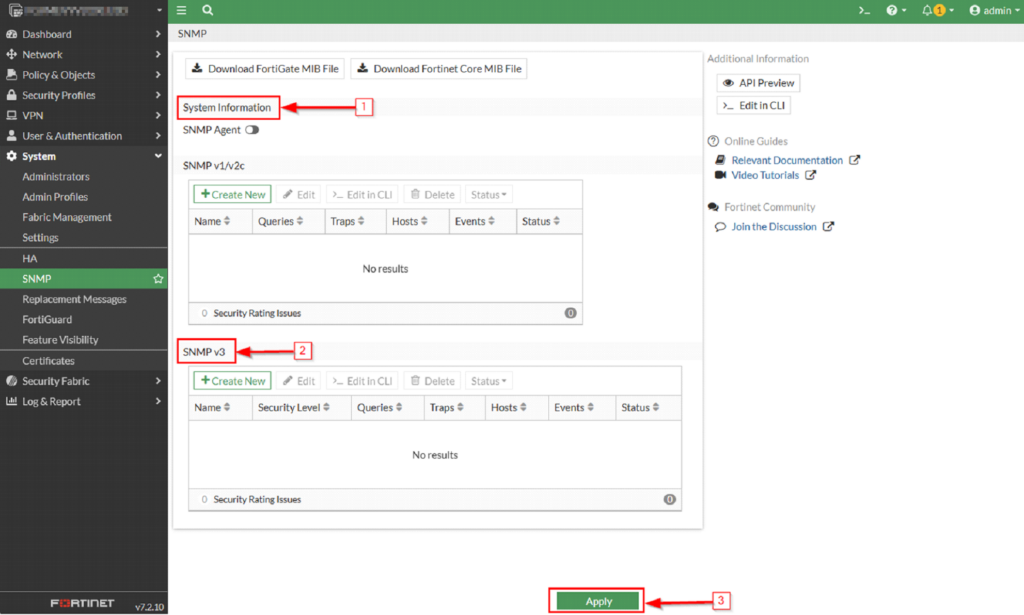
If no SNMP option is under the system, check the VDOM options, maybe global is not selected. This happens when the VDOM option is enabled. In that case, the SNMP option is visible under global VDOM.
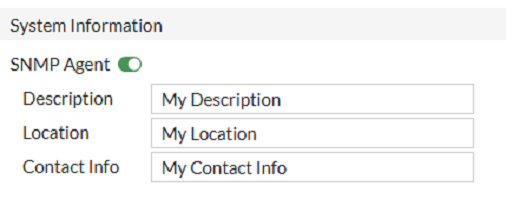
System Information
Enable the SNMP agent or snmpd and type your device Description, Location and the Contact info (enabling SNMP agent is the only mandatory activity here). An example is shown below.
Configure the SNMP community and protocols (section ”SNMP v1/v2c” or “SNMP v3”)
Click “Create New” button in the SNMP v3 section (or use SNMP v1/v2c in case you want to configure v1 or v2c).
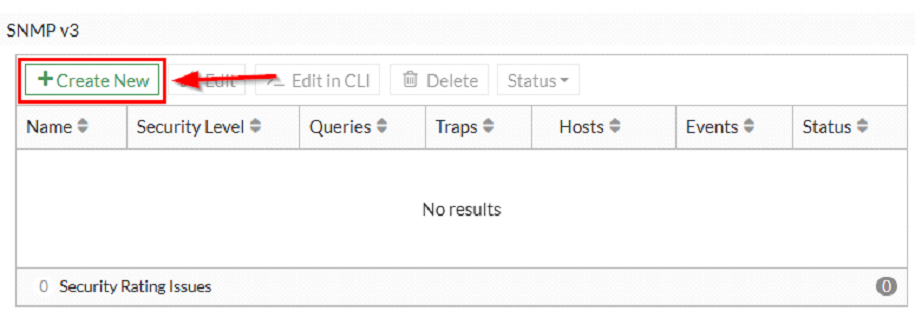
The following pop-up appears:
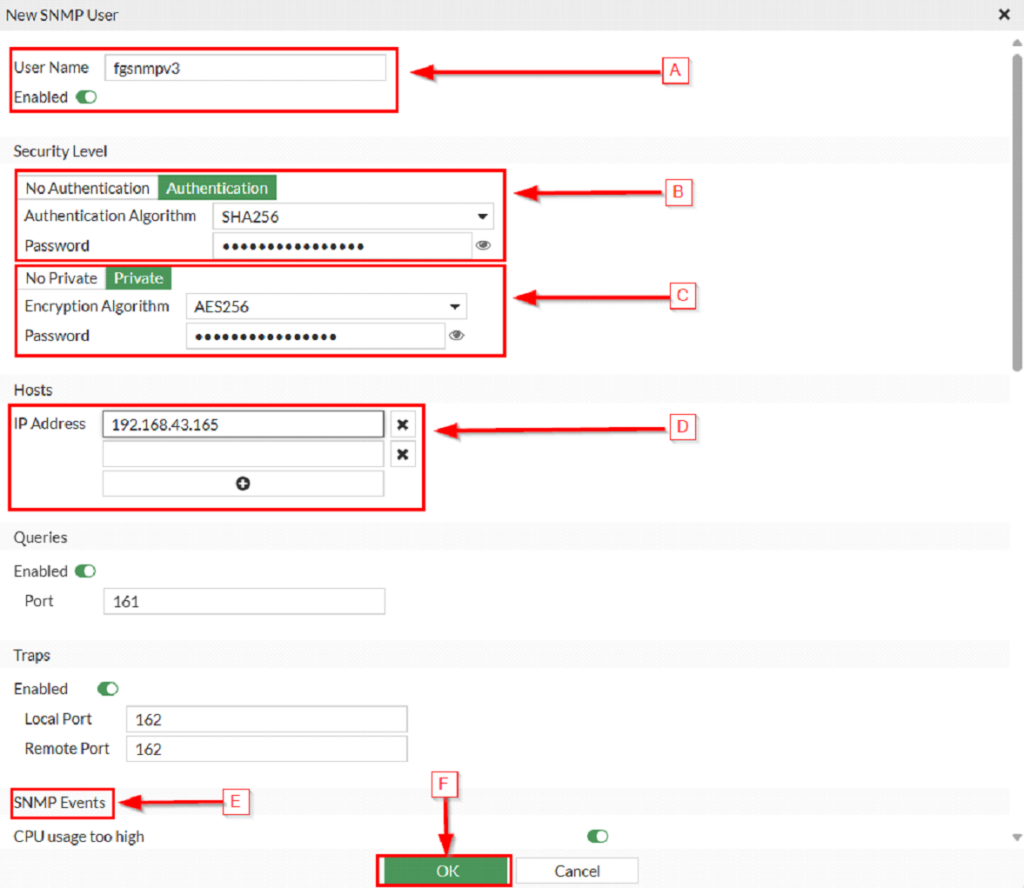
A. Set the SNMP v3 username and enable the configuration. fgsnmpv3 is used in this example.
B. Set the Authentication in the Security level section (if necessary). In case it is required (suggested configuration for a Firewall), set the Authentication Algorithm e.g. SHA256 (as shown in the picture) and type the Authentication password.
C. Set the Encryption in the Security level section (if necessary). In case it is required (suggested configuration for a Firewall), set the Encryption Algorithm e.g. AES256 (as shown in the picture) and type the Encryption password.
D. Set the allowed SNMP host, for our purposes set the Domotz collector IP (in our example it is 192.168.43.165). In case the Domotz collector has got more IPs (for instance if connected to more than one VLAN) then specify the IP which is used to reach the Firewall being configured.
E. Enable further SNMP Events, if necessary. In our case, it is not strictly required for Domotz to work correctly.
F. Press the OK button at the bottom of the pup-up to save the configuration.
Press the “Apply” button at the bottom of the page to save the configuration. This is very important, and everyone tends not to do it, so please bear in mind that it is a mandatory action.
FortiGate configuration via CLI
Connect to FortiGate via CLI on the GUI or though SSH using an administrator user.
– Enable SNMP on FortiGate port
Identify the Firewall interface or port or VLAN that will be used by the Domotz collector to query the FortiGate via SNMP. Let’s assume for the scope of this article that it is “port 1”. Show the port 1 configuration using the following command:show system interface port1
An output like this might be printed in the console:
config system interface
edit "port1"
set vdom "root" set ip 192.168.43.xxx 255.255.255.0 set allowaccess ping https ssh http set type physical set snmp-index 1
next
end
Let’s focus our attention on allowaccess attribute. Normally, SNMP is not enabled by default in the allowaccess. Add the SNMP protocol to the rest of the other already enabled administrative access for the port you want to configure. Then run the following commands, preferably one line at a time (read output messages and if ok then acknowledge pressing “y”).config system interface
edit "port1" set allowaccess ping https ssh http snmp
next
end
That is because administrative access “ping https ssh http” where already configured in this example so SNMP was the only protocol to add at the end.
Check that SNMP protocol was added to the Allowed administrative Access running again the following command:show system interface port1
The following output should be printed:config system interface
edit "port1" set vdom "root" set ip 192.168.43.xxx 255.255.255.0 set allowaccess ping https ssh http snmp set type physical set snmp-index 1
next
end
Showing that besides previously enabled protocols there is also SNMP.
– Enable SNMP agent and configure the SNMP connection details
Customize the following commands to set up the System Information:
config system snmp sysinfo
set status enableset description "My Description"set contact-info "My Contact Info"set location "My Location"
end
Actually, the only mandatory activity here is enabling the status. The other field might be used to enrich the SNMP retrieved information.
Customize the following commands to set up the SNMP community (here SNMP v3 is used and suggested).config system snmp user
# [A]
edit "fgsnmpv3"
# [B] set notify-hosts 192.168.43.165 set security-level auth-priv # [C] set auth-proto sha256 # [D] set auth-pwd my-auth-password # [E] set priv-proto aes256 # [F] set priv-pwd my-priv-password next
end
The italic text must be changed according to your environment as follows:
A. Set the SNMP v3 username. fgsnmpv3 is used in this example.
B. Set the allowed SNMP host, for our purposes set the Domotz collector IP (in our example it is 192.168.43.165). In case the Domotz collector has got more IPs (for instance if connected to more than one VLAN) then specify the IP which is used to reach the Firewall being configured.
C. Set the Authentication (if necessary). In case it is required (suggested configuration for a Firewall), set the Authentication Algorithm e.g. sha256 (as shown in the command).
D. Set the Authentication password.
E. Set the Encryption (if necessary). In case it is required (suggested configuration for a Firewall), set the Encryption Algorithm e.g. aes256 (as shown in the command)
F. Set the Encryption password.
Please use strong passwords for Authentication and Encryption.
Domotz Configuration
Using the Domotz dashboard explored view, open Collector and then click on the firewall you want to configure.
For instance, in my case it is Fortigate-Firewall device.
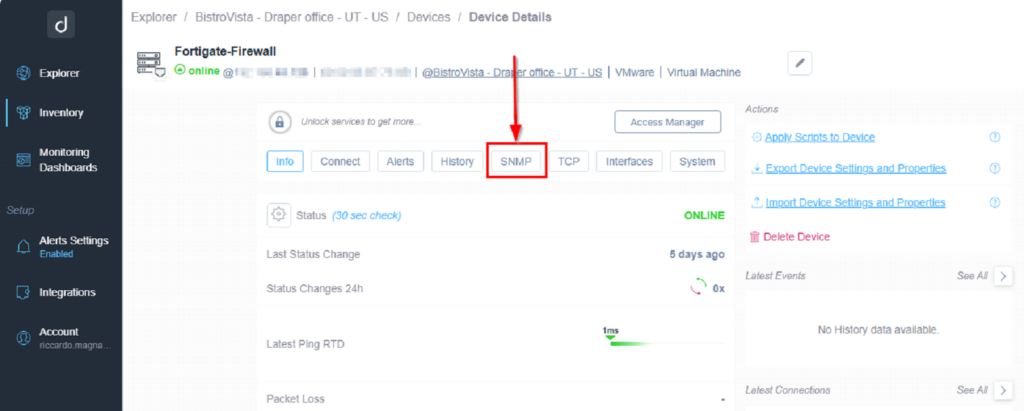
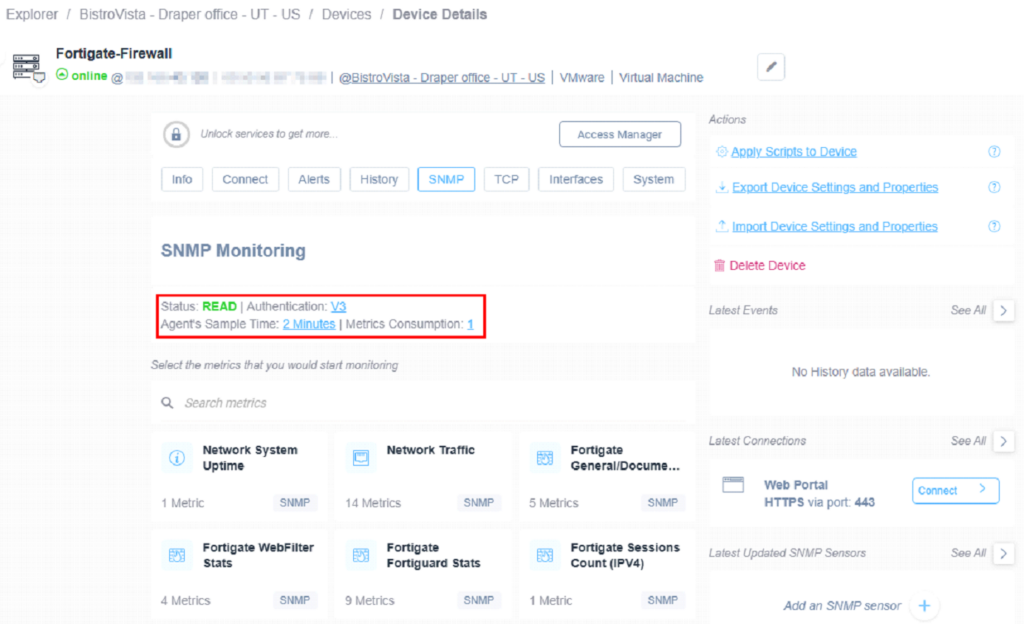
Open the SNMP tab:
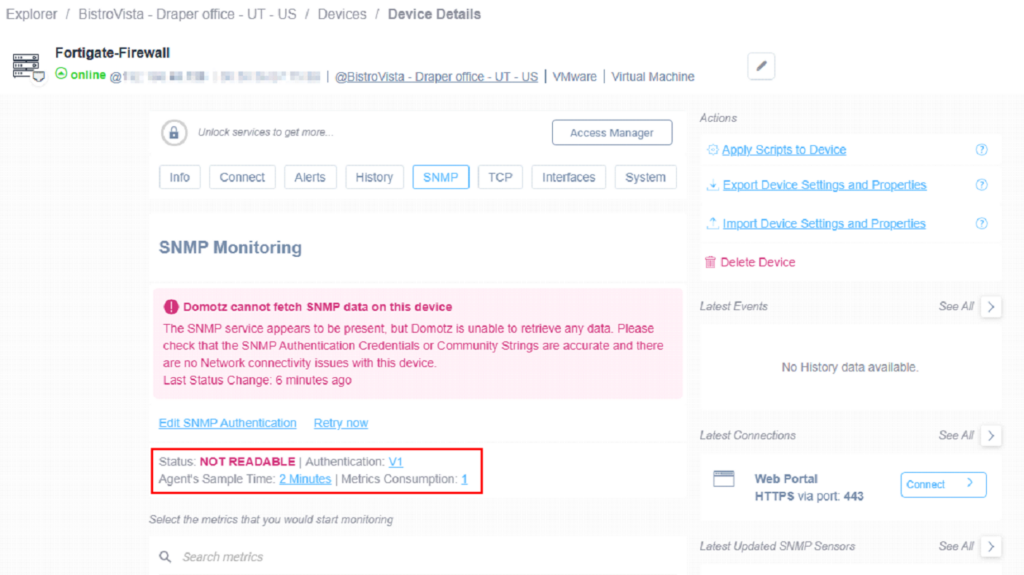
The SNMP status will be NOT READABLE initially (red).
Click the “Edit SNMP Authentication” hyperlink and then the following pop-up will appear:
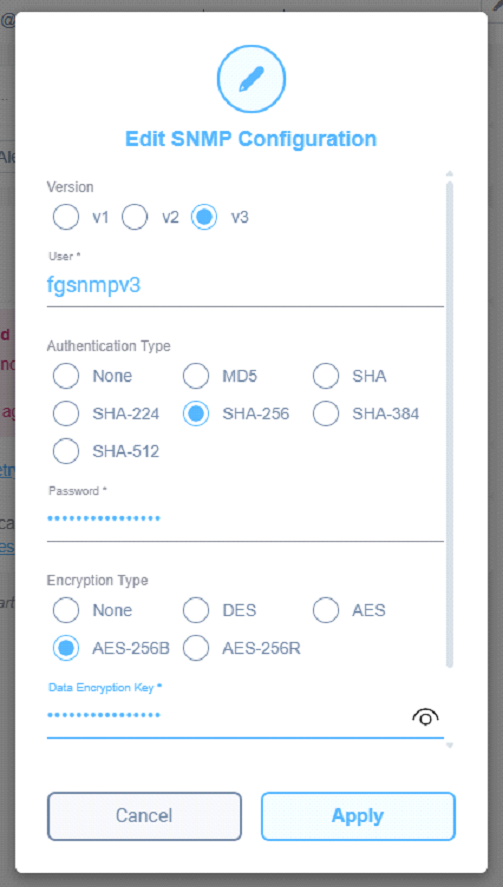
Set the same values:
⦁ Version: e.g. v3
⦁ Username: e.g. fgsnmpv3
⦁ Authentication type: e.g. SHA-256
⦁ Authentication password: e.g. my-auth-password
⦁ Encryption type: AES-256B
⦁ Encryption password: e.g. my-priv-password
in accordance with the parameters specified in the FortiGate configuration section, press “Apply”.
If everything was correctly set, then the FortiGate device on Domotz will result connected to the FortiGate real device:
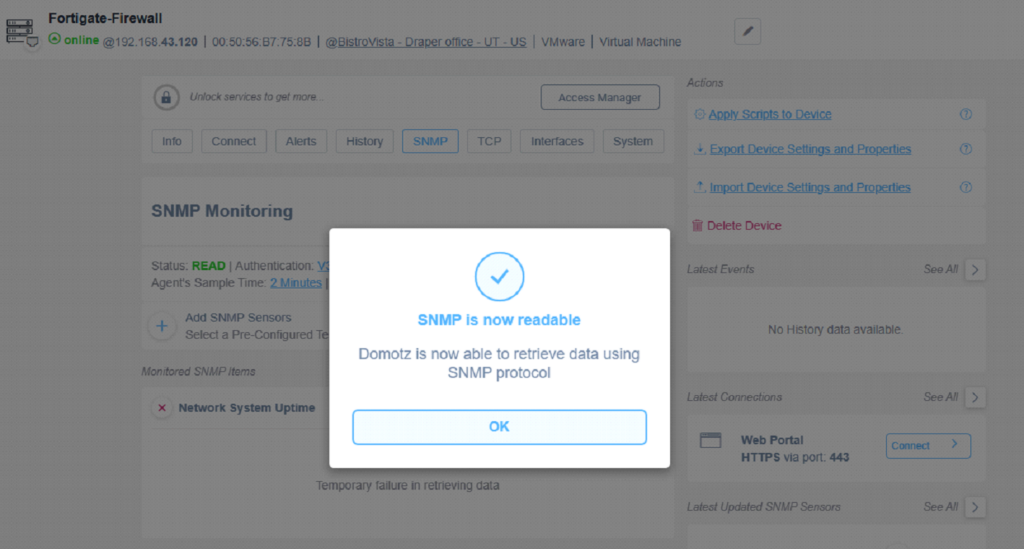
And the SNMP status should turn to READ (green).
More information
In case of problem or advanced configuration e.g. VDOM on FortiGate, please have a loot at the following articles:
https://community.fortinet.com/t5/FortiGate/Technical-Tip-How-to-Configure-FortiGate-SNMP-Agent-for/ta-p/196866
and
https://community.fortinet.com/t5/FortiGate/Technical-Tip-How-to-perform-queries-usning-SNMPv3-to-non/ta-p/335112

