The Remote Connection features allows you to connect to a device, with a single click.
The currently supported options include:
- Embedded Remote Connection for Web Services (HTTP, HTTPS), Remote Desktop (RDP), and Console Access (Telnet, SSH).
- Generic TCP Tunnel for remotely connect to virtually any single device through the mean of any TCP proprietary protocol. For example, this can be used to remotely program an Home Automation system like Crestron, Lutron, Savant, Control4, etc, or to access VNC Servers, or SSH via proprietary terminal client, FTP server, Apple Airport, and many others.
Feature Access
The feature is available from the Device Details screen, by clicking on the Connect Tab, as well as from the Remote Connections & VPN Tile.
The Domotz Agent automatically identifies whether a device is running any of the supported services (by checking on the most typical ports) and makes them available as clickable items as shown in the screenshot below.
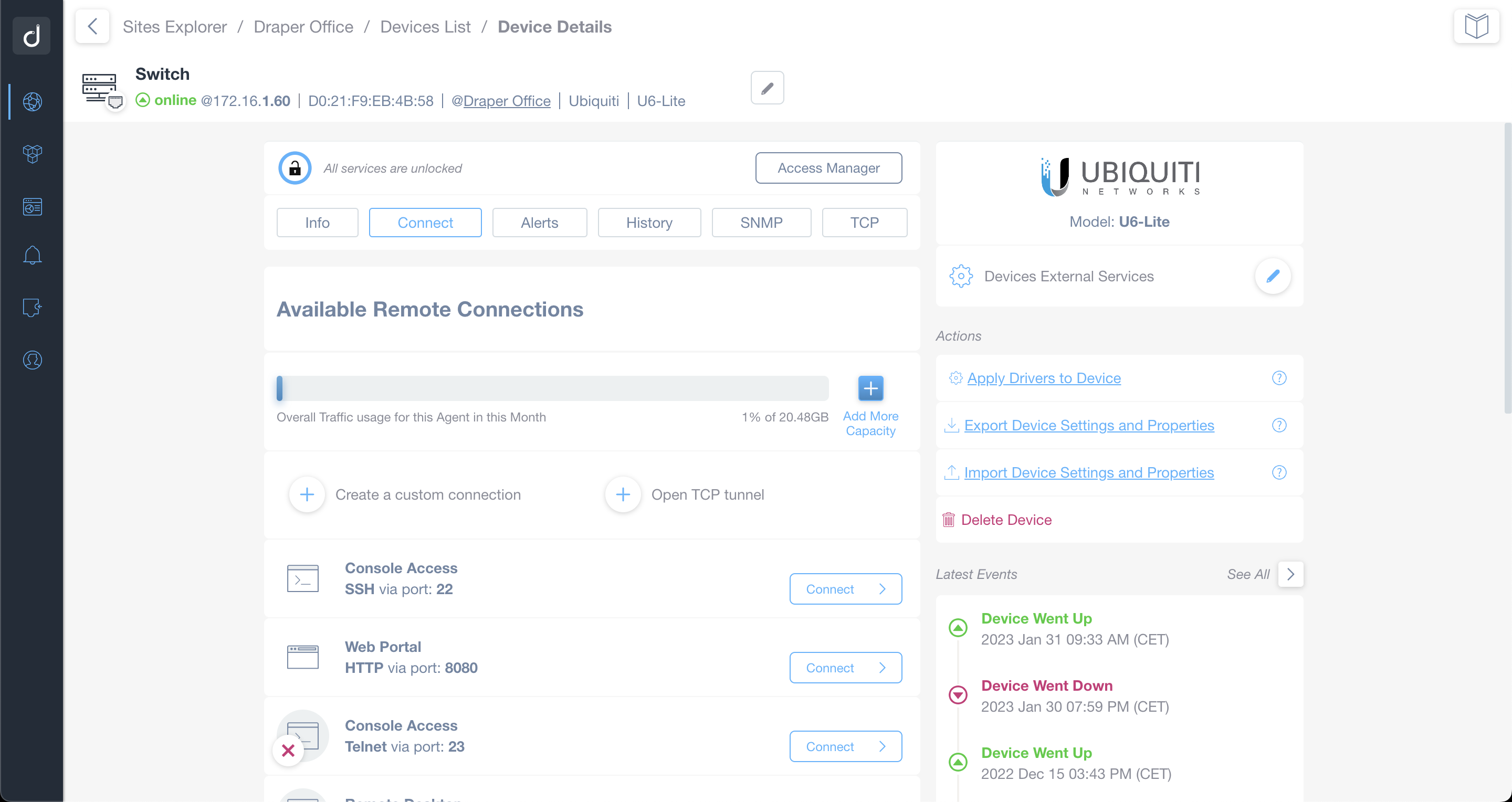
Create/Remove Custom Connections
The automated discovery only checks services on standard or typical ports.
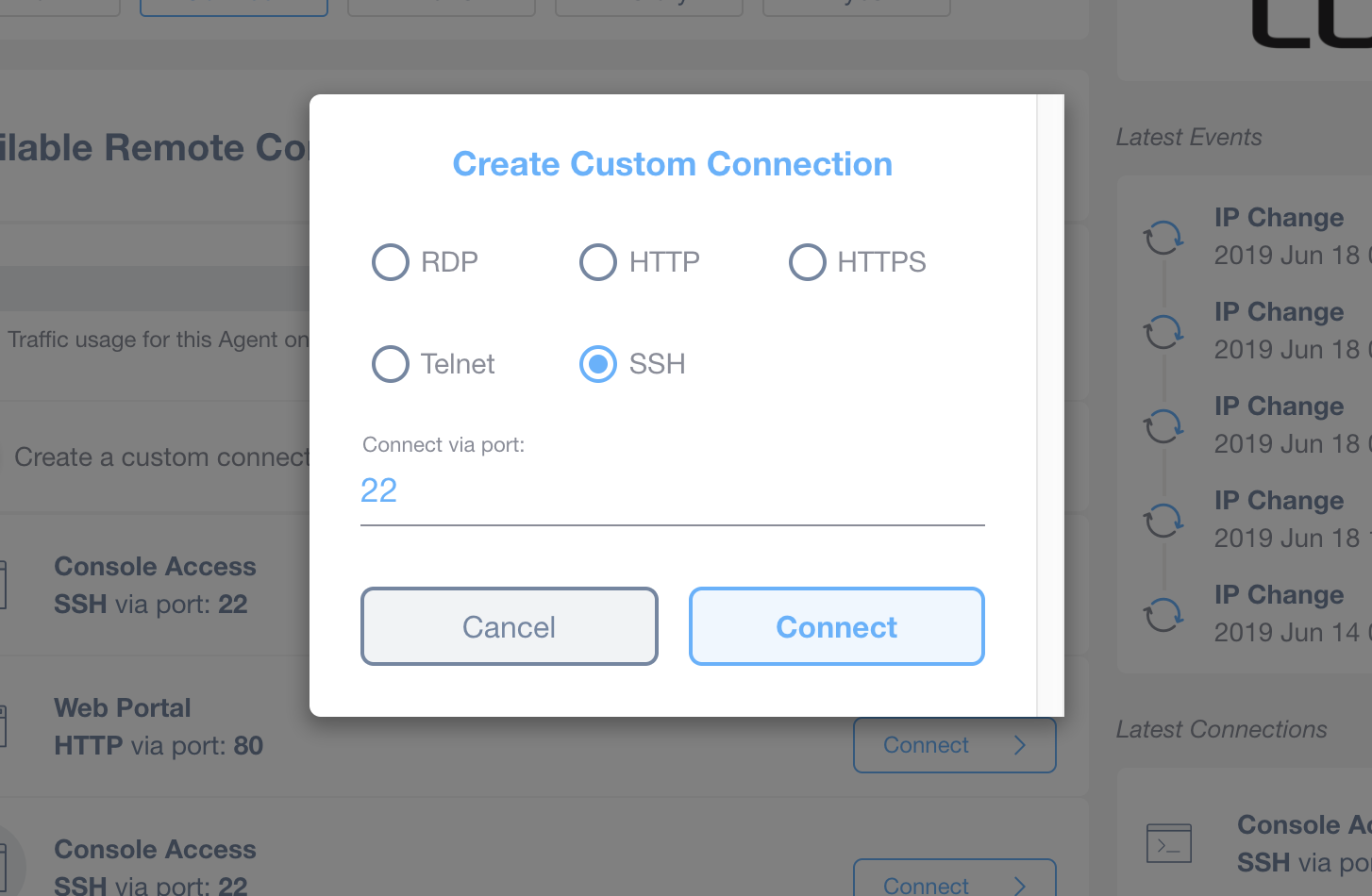
It is possible that, on some devices, these services are installed on different ports. In this case, if you know the port, you can create up to 8 custom connections for each device by using the Create Custom Connection button.
Custom connections feature a red “x” button allowing you to remove the connection.
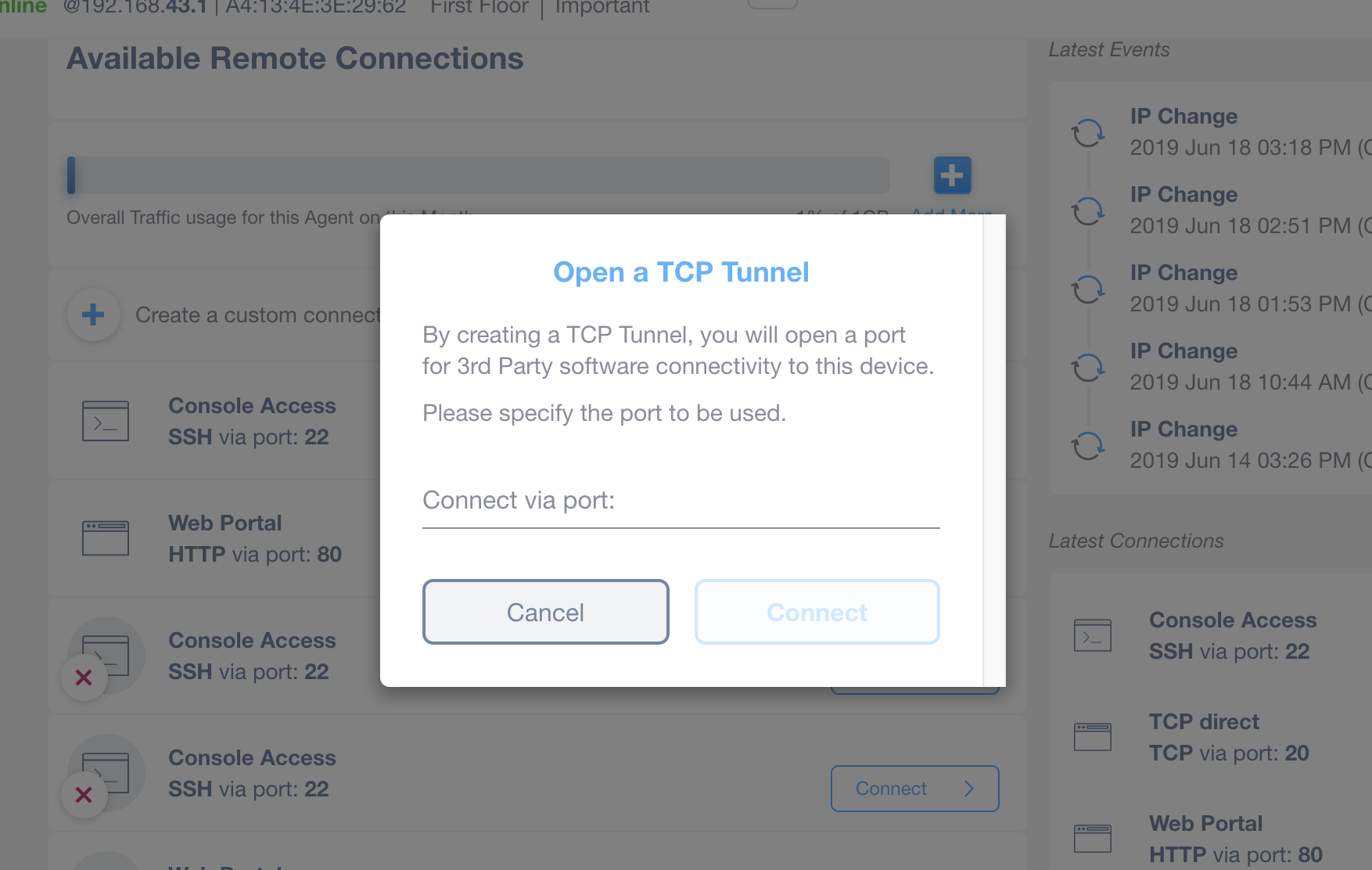
TCP Tunnels
It is possible to create a generic TCP Tunnel, by specifying a port to be used. Domotz will open a port allowing a 3rd party software to connect to the device.
Once the TCP Tunnel is created and in place, you can use the endpoint Host and Port of the tunnel into your local 3rd party software to remotely connect to the end device.
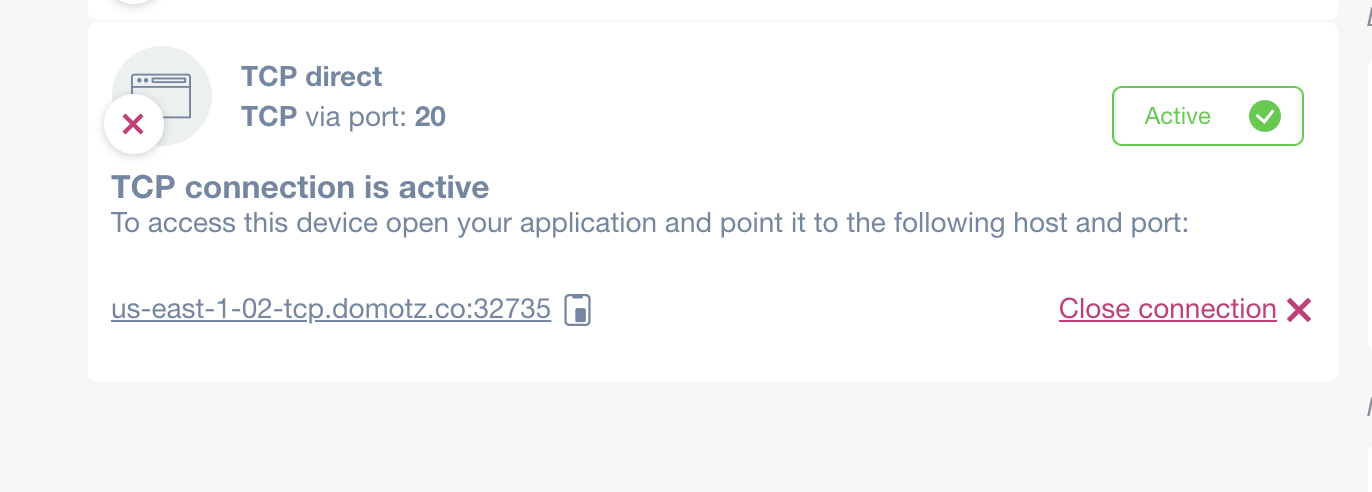
For security reason the Tunnel will be terminated in 1 hour since the creation. However, the connection can be closed at any time (“Close connection” button) and the configuration removed (click on the “X” on the TCP direct connection icon).
Security
Security Note: When clicking the Remote Connection (either HTTP or HTTPS, SSH or Telnet, or RDP), we establish a secure channel (Encrypted Overlay Network) between your home network and our cloud and an HTTPS channel between the App (either Mobile App or WebApp). Therefore the entire communication from the App to the Agent is encrypted (and nobody can sniff the content of it). Of course, the communication between the Agent and the end-device (e.g. a WebCam), if it is over a non-secure channel (e.g. http), is not encrypted, but that is only internal to the local network (We assume you trust your network, otherwise you wouldn’t have non-encrypted services).
Moreover, if you look at the URL when opening a Remote Connection through the WebApp, and you copy and paste that URL on a different PC/Client, you won’t be able to reach the end-device.
This has been designed in order to allow people to use the Domotz App even in a non-secure location: e.g., if you are in an Internet Cafe’, over a non-secure WiFi, anybody with a little bit of IT skills can identify the URL you are connecting to (even if it is over HTTPS). But with only that URL, the hacker can’t reach your home device.
Finally, the Domotz solution for the Remote Connectivity guarantees an additional level of security, given that all the supported protocols are encrypted when the data is exposed on the public network. Therefore, even the data for the Telnet and Http Remote Connection (which, by default, are not encrypted), with the Domotz solution, they are secured on the public network by this encrypted channel.
For more details about Domotz Security, please see the Domotz Security Whitepaper.
Troubleshooting Remote Connections
If you having issues when using this feature please check the following:
Firewall restrictions
Be sure that the following hosts/ports are allowed for outgoing connections:
us-east-1-sshg.domotz.co (range: 32700 – 57699 TCP)
us-east-1-02-sshg.domotz.co (range: 32700 – 57699 TCP)
us-west-2-sshg.domotz.co (range: 32700 – 57699 TCP)
sshg.domotz.co (range: 32700 – 57699 TCP)
Intrusion Detection\Prevention Systems
If you are using an IDS (such as Snort), remote connection over reverse tunnels can be blocked and identified as an “SSH challenge-response overflow exploit”.
In this case, in order to make the Remote Connections from Domotz working, you need to whitelist the security rules reported as “attempt to exploit” from the Domotz Agent when trying to use the Remote Connections.
In case of Snort, please refer to this rule for more information.
Domotz Snap Installation
If you installed the Domotz agent using the snap package, you may:
Snap Interfaces
Connect the snap interfaces
Please try to reconnect your snap interfaces in this order:sudo snap connect domotzpro-agent-publicstore:firewall-control
sudo snap connect domotzpro-agent-publicstore:network-observe
sudo snap connect domotzpro-agent-publicstore:raw-usb
sudo snap connect domotzpro-agent-publicstore:shutdown
sudo snap connect domotzpro-agent-publicstore:system-observe
The Kernel “Tun” module
And then check if the tun module has been loaded:
cat /etc/modules | grep tun
you should get an output like this:

if you do not get the “tun” output please run this commands:
sudo sh -c 'echo tun >> /etc/modules'
sudo modprobe tun


