This article will guide you step by step to deploy a Domotz agent with the Auto Discovery disabled by default and let you add only the devices that you would like monitoring based on their ip addresses.
Install the agent with scanning disabled on all interfaces
1) create an Agent Activation API Key in the Domotz Portal (https://help.domotz.com/user-guide/domotz-api/ )
and get the following parameters which you will need to customize the activation script:

2) Download this PowerShell script:
3) Customize the script by filling in the following parameters:
- $ActivationKey
- $ApiEndpoint
- $AgentName
4) Open a PowerShell with administrative privileges and run the script
5) Please access http://localhost:3000 to activate your agent (please use http and not https)
Check interface policy and define the ip/external host to be scanned
1) Create an Public API Key (which is different from the Activation Key – which you created earlier https://help.domotz.com/user-guide/domotz-api/ ) and get the following parameters which you will need to customize the curl API call:

2) Check the current agent scanning policy (customize the following curl by adding the following variables to the system or replacing them on be below examples):
- $api_key
- $endpoint
- $agent_id
N.B. you might find the agent id here:
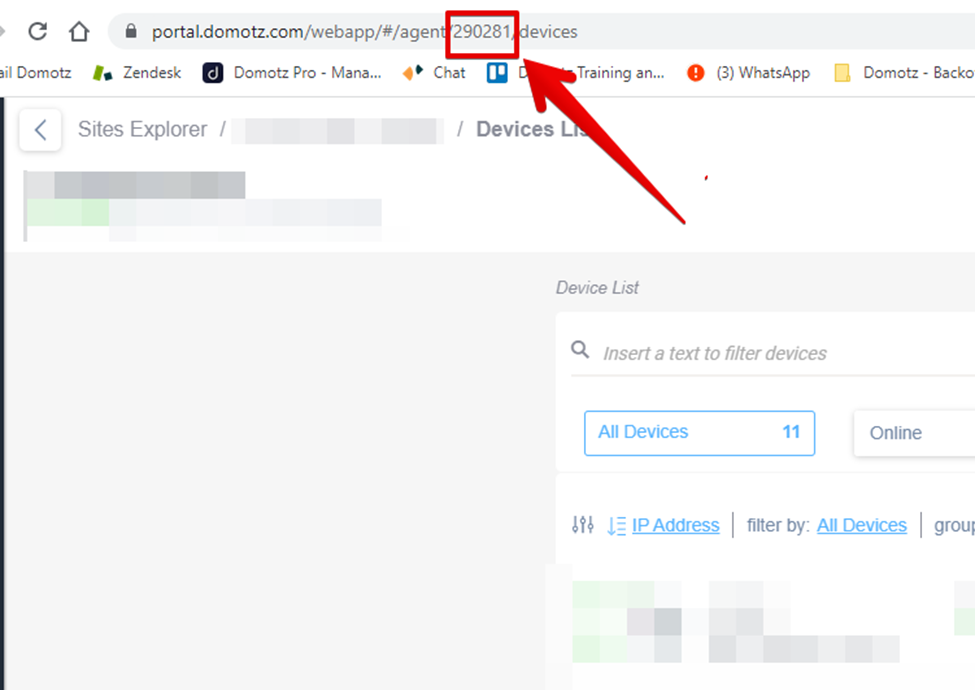
Run this curl from the windows command line:
curl -X GET $endpoint/agent/$agent_id/network/interfaces-policy -H "x-api-key: $api_key"You should get this output:
{"policy":"deny","rules":["*"]}And this means that the general policy on all interfaces is “deny”. In this case the Agent will not perform discovery unless you whitelist some devices.
3) Whitelist devices
For internal devices (that resides in the LAN where the Domotz agent is installed) instead, please create a file called json.txt with the following payload inside:
{
"forced_ip_addresses": [
"$first_ip", "$second_ip"
]
}(each ip address is listed as above in between double quotes, and separated by a comma).
And save it.
Then, launch the following curl from the command line:
curl -X PUT $endpoint/agent/$agent_id/network/ip-scan-policy -H "Content-Type: application/json" -H "X-Api-Key: $api_key" -d @json.txt
To test that the whiltelisted devices are in the scanning policies, please run this curl from the windows command line:
curl -X GET $endpoint/agent/$agent_id/network/ip-scan-policy -H "Content-Type: application/json" -H "X-Api-Key: $api_key"You should get this output (this is just an example with some ip addresses):
{"forced_ip_addresses":["192.168.143.2","192.168.143.234"]}

