How to enable configuration management (backup/restore) on Fortigate
- Ensure SSH is enabled, and that no login or message banners are configured (refer to the instructions below to disable banners).
- TFTP should be enabled and allowed at the firewall on both, the Fortigate and Collector host firewalls – Inbound and Outbound (see the warning below).
- SSH account provided for unlocking must be super_admin or admin
- The maximum limit for the configuration file is 5MB
- Hash for passwords and other encrypted data may be shown as different when comparing configurations even if the password is the same
- A firewall rule must allow TFTP traffic (inbound and outbound) from/to the Domotz collector host. For further information please check TFTP Session Helper
- The following configuration is needed for the correct interpretation of its configuration:
config system console
set output standard
endTo disable banners on a Fortigate device, run the following commands:
config system global
set pre-login-banner disable
set post-login-banner disable
endUnlocking FortiGate reachable through a Site-to-Site VPN (Routed Networks)
If communication between the collector and the FortiGate is routed through a VPN, the process may fail if the return path to the collector’s network is blocked due to the VPN interface lacking an assigned IP address.
For FortiGate devices, Domotz retrieves configuration files by triggering a TFTP transfer from the FortiGate to the Domotz Collector. However, when TFTP traffic is sent over a site-to-site VPN, the firewall uses the interface’s outbound IP address as the source. Since many VPN tunnel interfaces lack an assigned IP, these packets often default to 0.0.0.0 as the source address. Because site-to-site VPNs enforce strict access rules, traffic originating from 0.0.0.0 is typically rejected.
To avoid this problem, configure the VPN tunnel interface with an IP address that fits within the permitted range of the VPN policy:
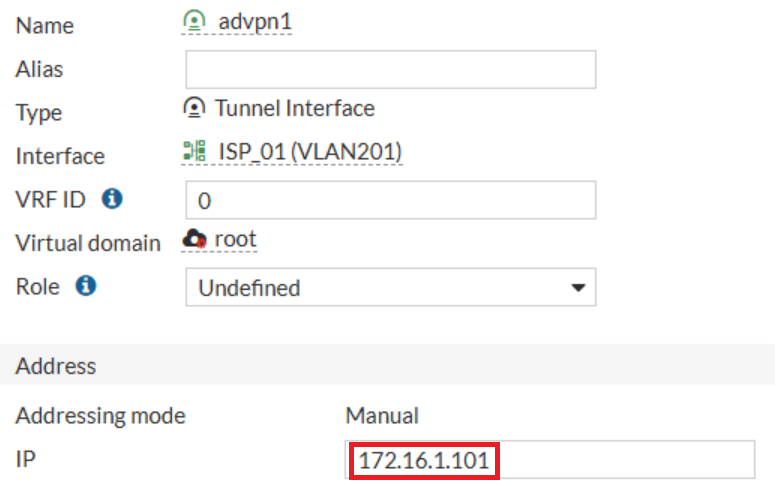
More details about it here: Configure IP address on an IPSec tunnel interface



