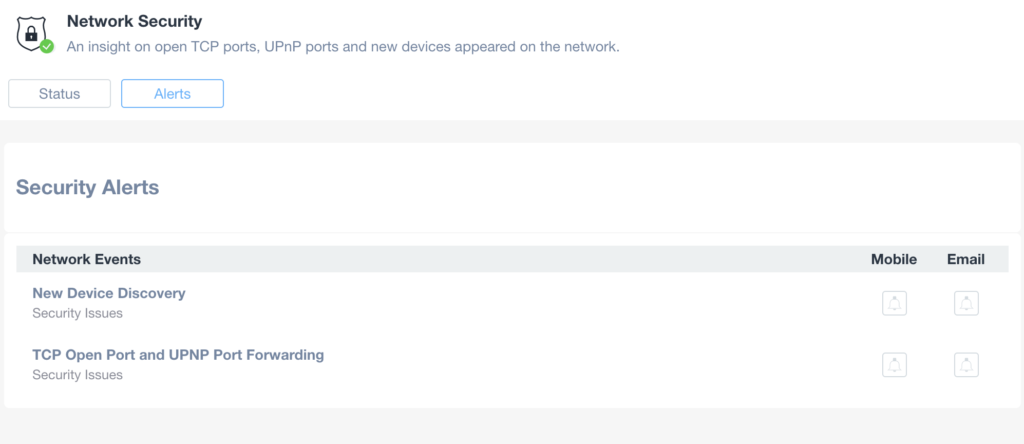
The Security feature gives you insights on potential threats to your network:
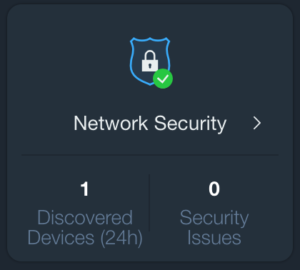
In particular, it provides the following information:
- Latest devices joining the network
- All Open TCP Ports on the WAN side
- Status of UPnP configuration at gateway level and attempts of leveraging that protocol
From this section, users can both review all the potential threats discovered or configuring alerts related to these perimeter scans:
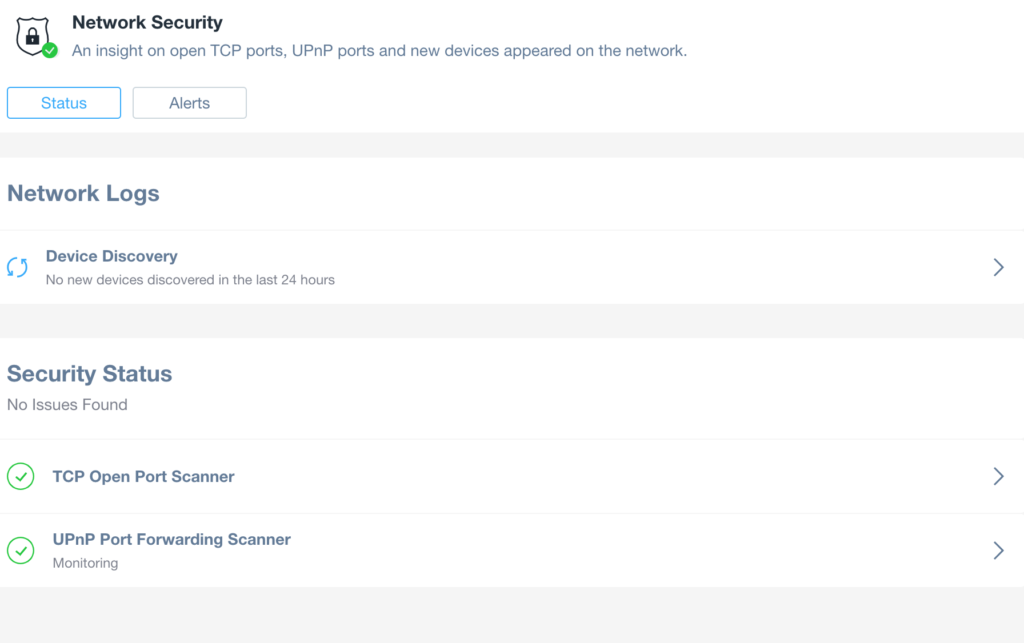
Network Logs – Device Discovery
This section will report all the devices discovered on the network in the last 60 days, starting from the most recent ones:
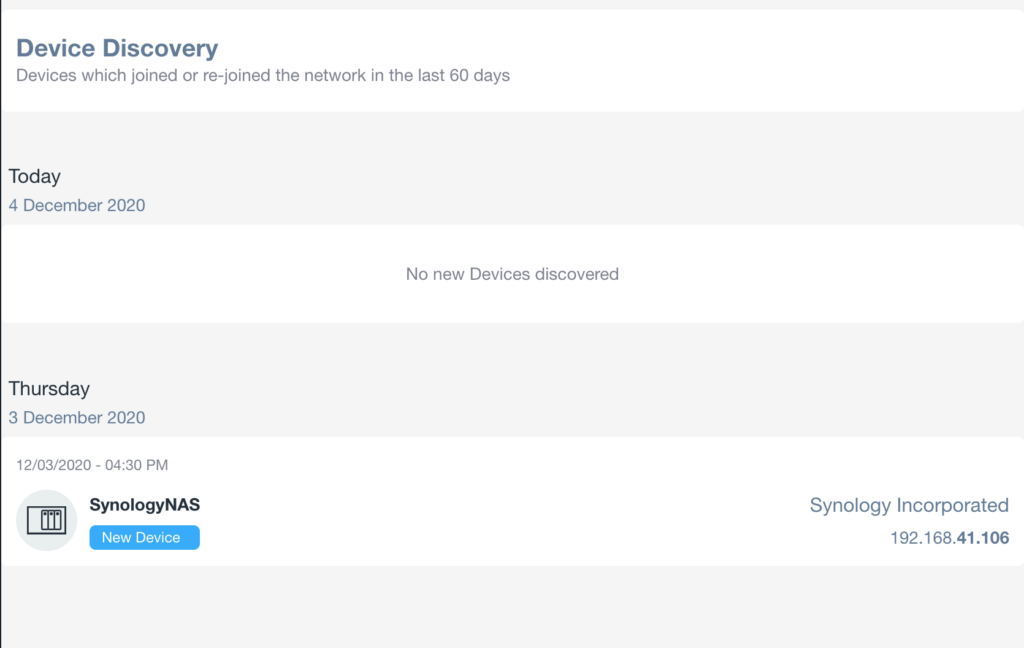
This information is very useful in order to understand if recently any un-expected device joined the network by acquiring an IP address.
Security Status – TCP Open Port Scanner (WAN Side)
When enabled, Domotz performs periodical TCP Port Scans from the Domotz Cloud against the public IP address of the network monitored (WAN IP Address).
The automatic periodical scans are performed with a quite slow process so that most automatic intrusion detection systems (IDS) are not capable of blocking the requests from the Domotz Cloud, increasing the accuracy of the scan.
The automatic TCP open port scanner can be enabled inside the related page.
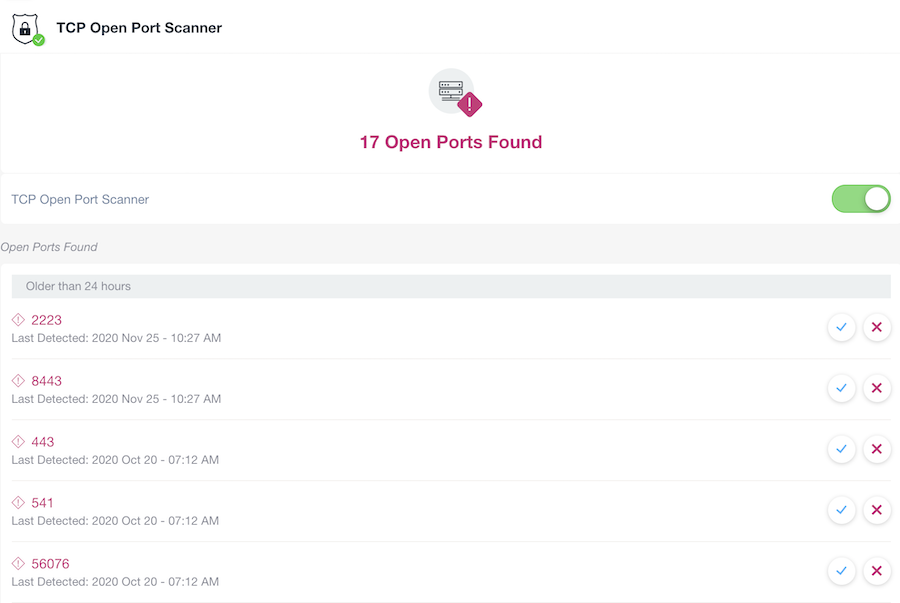
A discovered opened port is a potential threat to the network, especially if combined to a default password of the device reached through that port.
The discovered opened ports which are identified by Domotz can be marked as safe or removed in case they have been closed:
- Safe: a discovered opened port which is marked as “Safe” is recognized by the Domotz User as required on that network, and it will not be reported as a threat on the higher level dashboard. They will not reappear in the list of discovered opened ports. The Domotz user acknowledges that the port is opened and it is safe to be so.
- Removed: on the other hand, if the user removes one discovered opened port, it means that the user has resolved the potential threat (e.g. closing the port on the WAN side of the gateway, removed the Port Forwarding, etc). In this case, if the Domotz Cloud will discover again the same port as open in a subsequent scan, the port will be reported again as a potential threat.
Security Status – UPnP Port Forwarding Scanner (LAN side)
When enabled, Domotz performs periodical UPnP Port Forwarding scans from the Domotz Agent against the primary gateway device (to check whether the UPnP Port Forwarding mechanism is enabled). Moreover, the Domotz Agent will also monitor for any device internal to the network which is trying to leverage the UPnP capabilities of the Gateway to open ports and enable port forwarding to it.
When enabled, Domotz performs periodical scans against the Gateway and monitors all the devices within the network.
The automatic UPnP Port Forwarding Scanner can be enabled inside the related page.
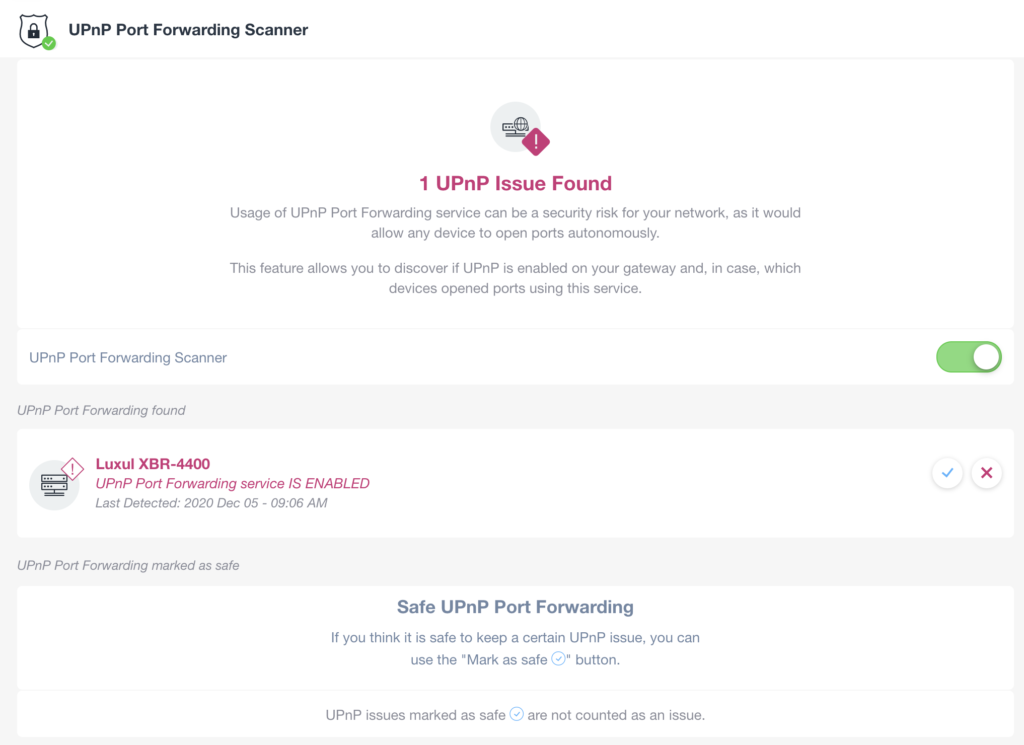
The gateways which are identified by Domotz with UPnP Port Forwarding enabled, and the devices trying to leverage this capability can be marked as safe or removed in case they have been resolved:
- Safe: a discovered UPnP Port Forwarding device (either the Gateway itself or all the devices attempting to leverage this capability) is marked as “Safe” is recognized by the Domotz User as required on that network, and it will not be reported as a threat on the higher level dashboard. They will not re-appear in the list of discovered opened ports. The Domotz user acknowledges that the UPnP Port Forwarding is required it is safe to be so.
- Removed: on the other hand, if the user removes one discovered UPnP Port Forwarding possible threat, it means that the user has resolved it (e.g. disabling UPnP Port Forwarding on the gateway, identified devices removed, etc). In this case, if the Domotz Agent will discover again the UPnP Port Forwarding as enabled (or device attempting to leverage it) in a subsequent scan, the same will be reported again as a potential threat.
Security Issues Alerts
From inside the Security tab, in the Alerts sub-tab, the user can enable which type of Alert he wants to receive in case of any potential security threat discovered on the network: